Prelog
There are people in this world you assume you'll run into again since they always loop in and out of your life. The moments with them are always better for it. A friend passed this weekend which gave me insomnia. -vgr
Introduction
DNS is known to be unencrypted. To solve for this problem DNS over HTTPS (DoH) and DNS over TLS has been developed. However, this doesn't protect you from your DNS provider from using your data in ways you may not agree with.
This is why DNS over HTTPS over TOR can provide you with (mostly) anonymous, secure, DNS.
To get started:
- Install Ubuntu 20.04
git clone https://github.com/vgrsec/pihole-tordns.gitfrom github- Run
setup.shas root - Done.
This project combines pihole, a DNS adblock server, DNSCrypt-Proxy which allows for proxying DNS Queries over https, and TOR so that your DNS provider is unable to associate your DNS queries with you. DNSCypt-Proxy also provides DNS Caching, so that additional queries after the first one don't leave your network for the duration of the cache life.
If all you need is pihole with https, check out this blog by Sean Wright. It's quite good and all you need.
DNS Options
Lets walk through each type of DNS configuration
DNS
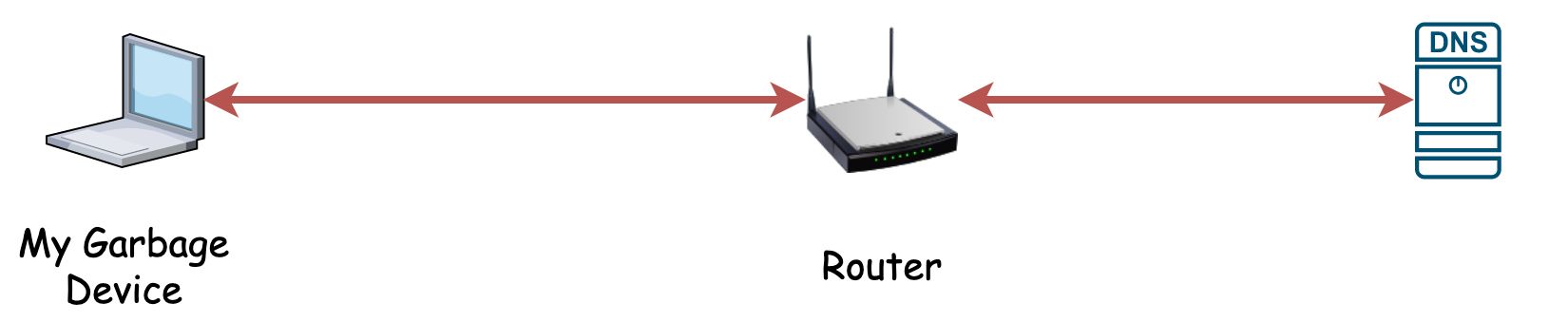
Most individuals at home have a router, which uses a default DNS server. The traffic from their laptops to the router is unencrypted, then the traffic from the router to the DNS server is unencrypted. This means anyone between your network, and the dns server will learn that you queried boogieblocks.com today.
Additionally, these DNS servers do not provide any filtering of malware, ads, or otherwise unwanted material. This is GOOD! A free and open internet relies on the open exchange of information and DNS providers censoring content by default should not be encouraged. This is why individuals install adblock and antivirus software on their laptop.
Pi-Hole DNS
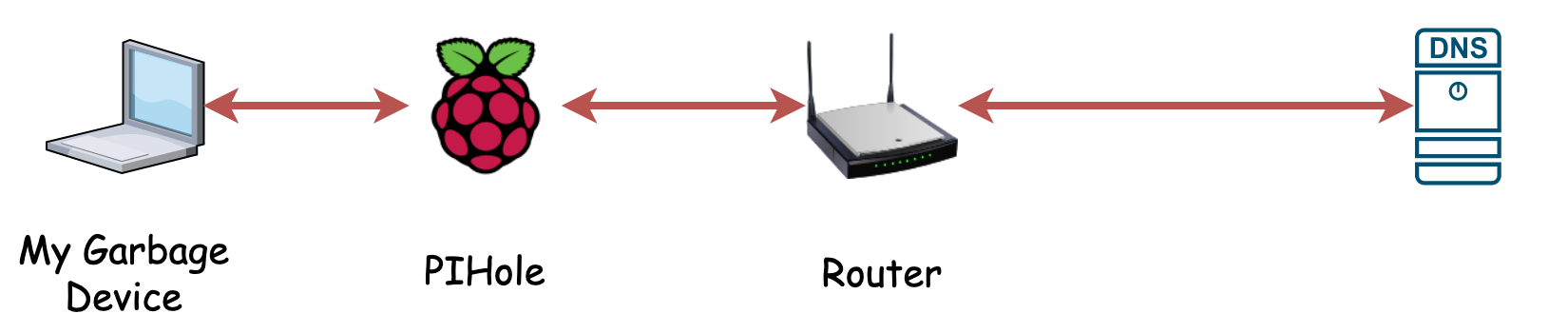
A common pattern for technologists. They setup a PiHole in their house to provide housewide adblock capabilities. Instead of the router providing DNS, a raspberry pi with pihole does. This allows for filtering of ads for any device on the network.
However, this doesn't secure your DNS traffic to your upstream DNS provider (DNSSEC is not encryption). Therefore anyone between your network, and the dns server will learn that you queried boogieblocks.com today, but if boogieblocks.com had ads, those ads would be blocked from showing up in your browser.
Pi-Hole DNS with DNS over HTTPS
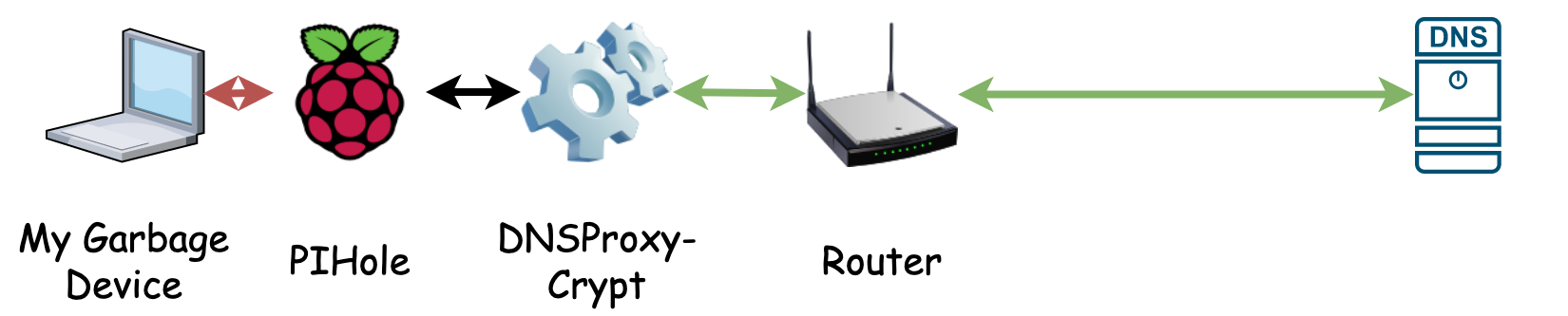
Unencrypted DNS is a solved problem. Today, DNS over HTTPS or DNS over TLS allow for encrypted DNS. Even some routers come off the shelf with this capability! Adding DNS over HTTPS to a pihole requires some command line work, but is achievable with well written blogs.
Encrypting your DNS queries does not protect you from your DNS provider. The DNS provider can still can associate your queries with you. Therefore, while no one between your network and the dns server will learn that you queried boogieblocks.com, your DNS provider will know you queried boogieblocks.com.
Pi-Hole DNS with DNS over HTTPS with TOR
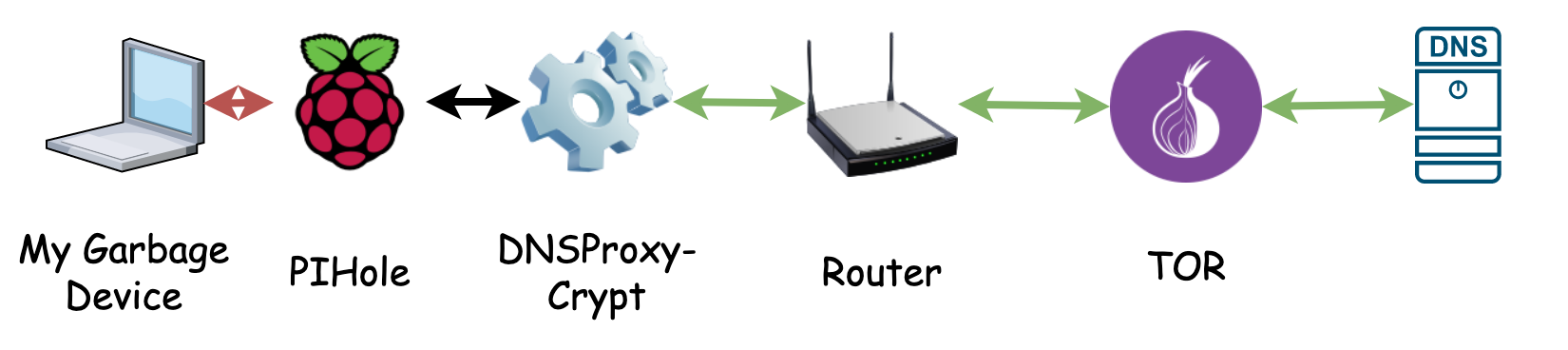
TOR is used for all sorts of unsavory reasons. However, the principal community are focused on internet freedom. Use the TOR network to route your DNS traffic and break the connection between your network, and your DNS query.
By routing your DNS traffic over TOR, over HTTPS, you accomplish a couple of things. First, the TOR network doesn't know what you're querying, all they see is HTTPS traffic. Second, the DNS provider sees DNS Queries from the TOR network not from you. Therefore no one but you will know you queried boogieblocks.com today.
The downside to this setup is that your first time DNS queries will have 600-700ms latency. This is unsolvable due to the way TOR works. Fast, Secure, Cheap. Pick 2. You can mitigate additional query speed by adding caching on your pihole which DNSCrypt-Proxy supports.
Finally, this isn't a solve all for privacy, your web traffic isn't going over tor. If anyone cared enough, they could associate boogieblocks.com with 69.36.46.2 and probably determine you went to boogieblocks.com.
Validation
The following videos and PCAPs show different setups and how I validated that my setups are working as intended. There were a couple of projects I found on github where the setup looked good, but when looking at wireshark, the project didn't accomplish what was intended.
View these full screen to read terminal/wireshark.
| PCAP Download Link | |
| PCAP Download Link | |
| PCAP Download Link (Note pcap shows query to spacejam.com not boogieblocks because I didn't save the boogieblocks query) |
Conclusion
This is a solution that can help reduce your personal data emissions from your house, while also giving you the benefit you wanted in the first place. To browse the internet and reduce the number of ads you see on websites.
Resources
- https://blog.sean-wright.com/dns-with-pi-hole-dnscrypt/
- https://github.com/piskyscan/dns_over_tls_over_tor/blob/master/README.md
- https://github.com/DNSCrypt/dnscrypt-proxy/blob/master/dnscrypt-proxy/example-dnscrypt-proxy.toml
- https://github.com/DNSCrypt/dnscrypt-proxy/wiki/DNS-server-sources
- https://dnscrypt.info/public-servers